Getting all user and security group access permissions across a Fabric Tenant
- Brunner_BI

- Jan 4, 2025
- 3 min read
Updated: Apr 25, 2025
In the times of Microsoft Fabric, access rights are getting more and more complex. Power BI itself already offers a wide range of item- and workspace-level access but in Fabric there are just a ton of items available.
In this blog post, we will show how you can get information on:
-See who has access to most Fabric items in your tenant
-Find out who has access to which workspaces (Fabric/Premium, Pro, PPU and Personal ones)
-Get a list of all access a user or security (Entra) group has
Which options do we have to get this?
For workspaces, in the admin portal, we can get this one workspace at a time. This is a very manual process though.


If we want to automate this, we can use the PostWorkspaceInfo API call to get it for one workspace (this does not include Personal workspaces though).
We can also include the getArtifactUsers URI Parameter to include item-level permissions. We still need to do some coding here and loop through all workspaces.
We can also take advantage of paid tools to get everything done without coding a single line. With Measure Killer, we can get all access rights quickly and in a nicely formatted way. Even reaching into Personal workspaces which are not possible with the solution mentioned above.
Request a free trial here to get started.
To start, open Measure Killer and select the "Tenant Analysis" mode:

After authentication, you can set some filters which are very useful in larger tenants. Select the ones that fit your needs and click on "next". The Access tab is the relevant one in our case, make sure to have it checked.

When MK finishes the analysis, click on "Access":

Now we can select different views, each one displaying access from a different perspective.
As a limitation, Measure Killer can't obtain the members of a security group, since this is part of Microsoft Entra and cannot be queried from within Power BI. You can get the full picture by joining the members of a security group with the Measure Killer output (see export options at the bottom of this post).
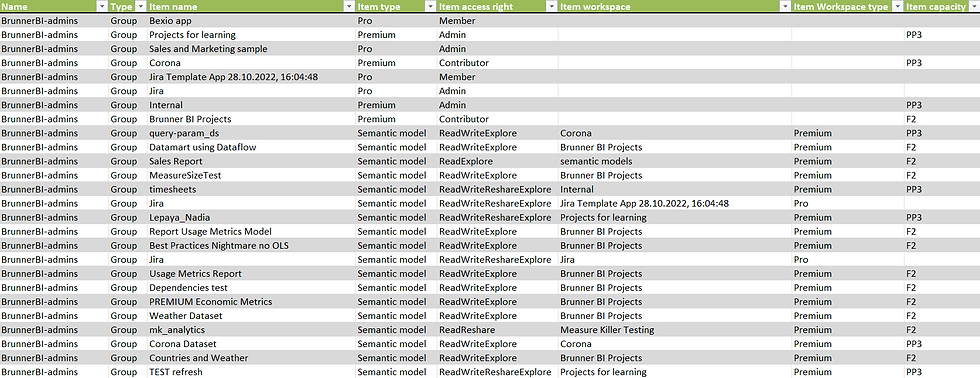
User/group level access
In the "User level" view, all the Fabric items supported by Measure Killer that a user or security group has access to are shown:

Workspace-level access

Item-level access
All other options are related to different Fabric items showing us who has direct or indirect (via the workspace) to an item including the type of access right.

Now let us look at some advanced stuff, I want to see who has been given access to a report in someone's personal workspace.
The tool highlights all users that were granted access to a Power BI report in somebody else's personal workspace.

This is very interesting information since this "Shadow BI" or however you want to call it can really get out of hand. Admins have very little knowledge about what is going on in personal workspaces.
We can also do other searches like who was granted "build" (ReadExplore is the technical definition) access to a semantic model.
Exports
Every view provides the option to do a custom search or to export to json or Excel. After exporting, the Excel file can be further explored to get more insights.

We can also export all access via a large .json file to do some further analysis or to share it with a colleague.
Get a free trial of these features (Measure Killer) here.


Comments